Unveiling the Layers: A Journey Through the OSI Model
A beginner-friendly guide using restaurant analogies
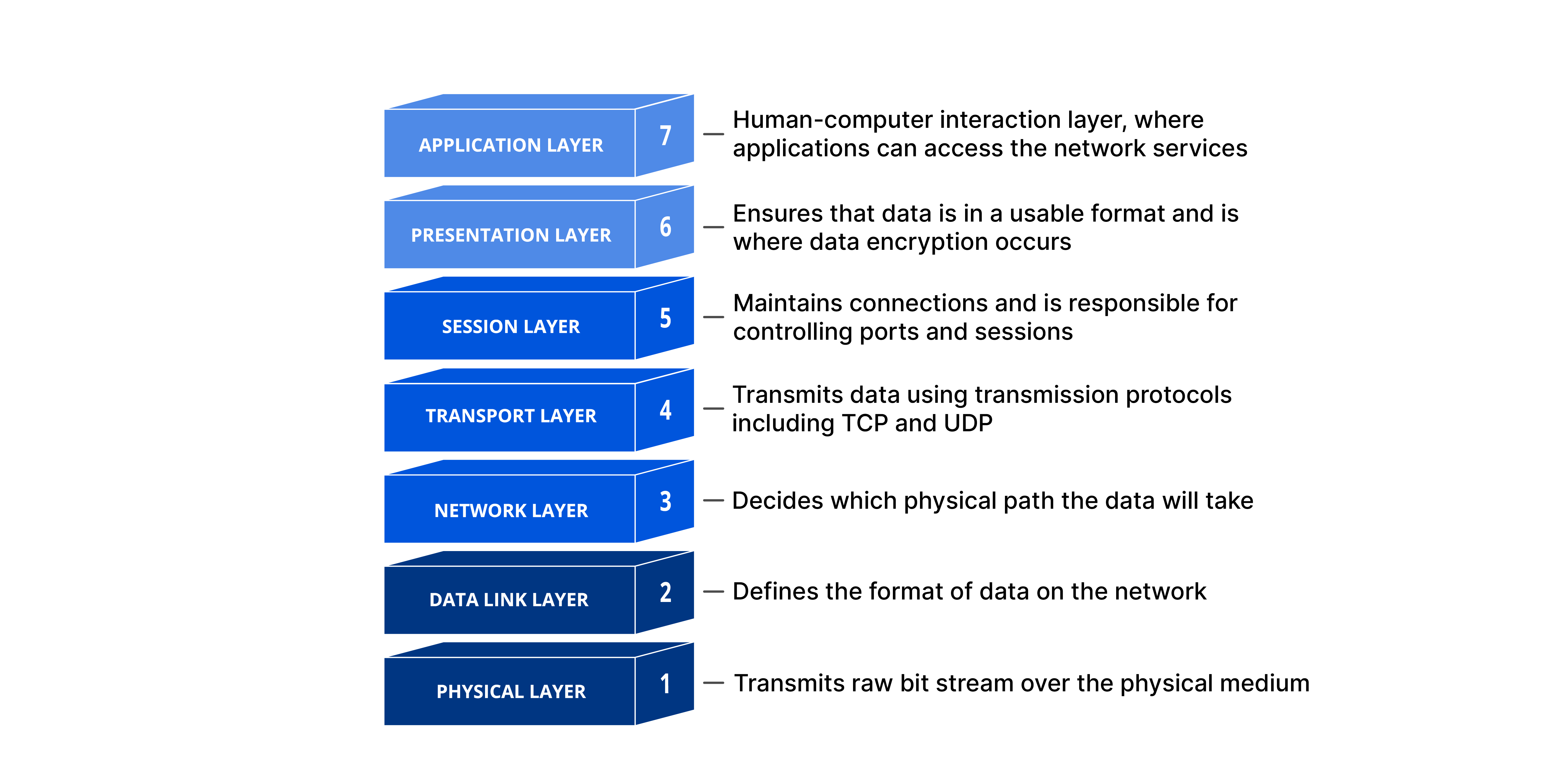
TLDR:
OSI-Open Systems Interconnection-is a seven-layer model that standardizes the way devices communicate over a network. This facilitates interoperability and provides for modular design; network communication is conducted in terms of these layers:
Application: Provides network services directly to users; it includes, for example, browsing the web, e-mail, and similar examples.
Presentation: Handles data formatting, encryption, and compression for compatibility.
Session: Manages sessions, including setup, maintenance, and termination.
Transportation: Reliable data transfer by segmentation, flow control, and error control is done with the help of TCP/UDP.
Network: It decides on which path the data will travel using IP addresses and routing.
Data Link: Detects errors, provides MAC addressing, and framing of data in a network segment.
Physical: Transfers raw bits over cables, wireless signals, or other physical media.
Each of them has a different role, yet all work in harmony to provide a smooth process of communication. The OSI model provides invaluable assistance during troubleshooting, design, and understanding networks.
Introduction:
The OSI (Open Systems Interconnection) model is a conceptual model for understanding and implementing network communication. It was created by the International Organization for Standardization (ISO) in 1984 to standardize networking protocols and enable interoperability between differing systems.
The OSI model consists of seven layers, where each layer plays a unique role in the process of communication. The hierarchical layers of abstraction move from bottom to top from the physical layer (hardware-related) to the application layer (user-related). So, let us explore each layer in depth.
Fun Fact: The name "OSI" was almost "SIO" (Standard International Organization), but they realized it would sound too much like a disappointed sigh!
Application Layer:
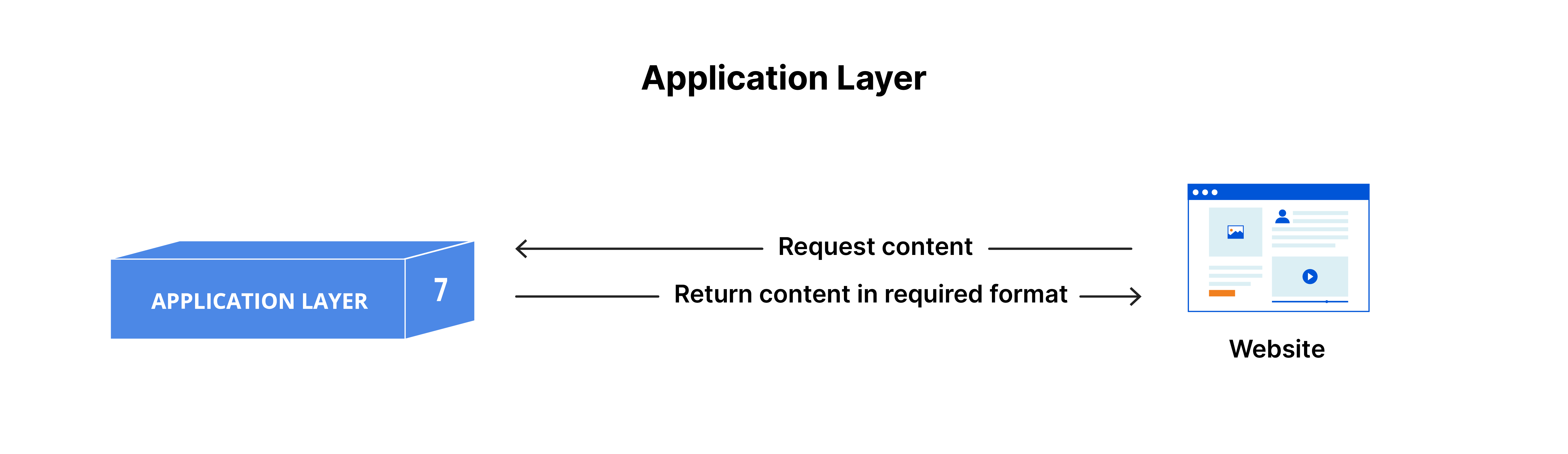
Application layer is closest to the end user and this is where the user interacts with the application. It receives user data is generated and from where the request originates and acts as a portal to provide network services to application.
Popular Application Layer Protocols:
HTTP/HTTPS: The backbone of web browsing
SMTP/POP3/IMAP: Your email's best friends
FTP: The moving company of the internet
DNS: The internet's phone book
Popular Presentation Application Protocols:
IDS/IPS (Intrusion Detection/Prevention Systems)
Application Proxy Servers
Application Gateways
Real-Life Analogy:
Think of a restaurant menu. The customer, interact with the menu or application layer to request dishes or services. The menu translates customer needs in question-terms of hunger-into specific items that the kitchen, or network, understands.
Presentation Layer: The Universal Translator
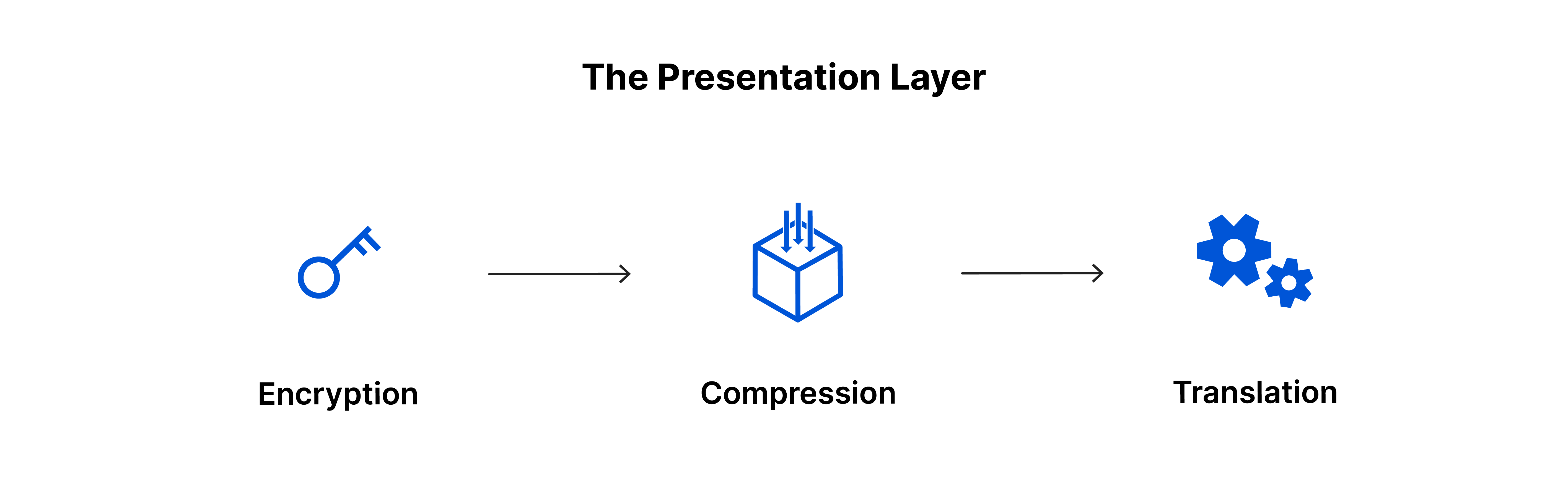
Presentation layer also known as Translation Layer is responsible for transforming the data such that it can be used and understood by Application Layer. This layer is responsible for handling tasks like data-encryption to protect during transmission, data-compression to reduce the size of data for efficient transmission, data-translation - converting data fomats (e.g. EBCDIC to ASCII))
Popular Presentation Layer Protocols:
SSL/TLS (Secure Sockets Layer/Transport Layer Security): Encrypts data for secure transmission
JPEG, GIF, PNG: Handles image formatting and compression
ASCII, EBCDIC: Manages character encoding and data conversion
MPEG: Handles video and audio compression and encoding
Network Devices operating on Presentation Layer:
SSL/TLS Accelerators
Encryption/Decryption Devices
Protocol Converters
Real-Life Analogy:
The waiter places your order and makes sure that the kitchen gets it right: If you ordered "medium rare" - a specific format request - the waiter ensures the chef cooks it to order. Encryption locks a delivery box so that when it arrives you can be certain that it is not tampered with.
Session Layer: The Digital Traffic Controller
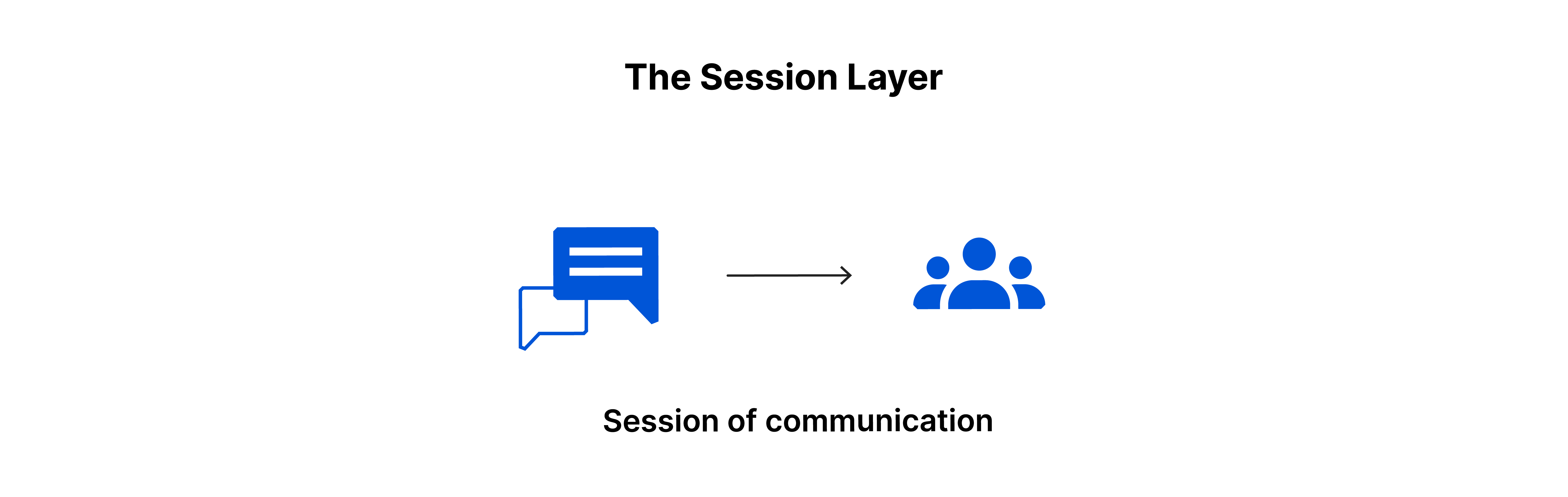
Session Layer is responsible for managing ,controlling and terminating the communication between two applications. This layer makes sure that the data exchange happens in an organised and synchronised manner.
Popular Session Layer Protocols:
RPC (Remote Procedure Call): Enables programs to execute procedures on remote systems
PAP (Password Authentication Protocol): Provides basic password-based authentication
SIP (Session Initiation Protocol): Manages multimedia communication sessions
Network Devices operating on Session Layer:
Session Border Controllers
NetBIOS Gateways
Authentication Servers
Real-Life Analogy:
It's like saying it's a session, like making a reservation at a restaurant. It's like the host seats you, sets up your table for you, and it's a session. If you need to pause, say take a phone call, then it keeps your table reserved.
Transport Layer: The Quality Assurance Department
Transport Layer is the layer where it gets decided how the data will be transferred over the network in a reliable manner using TCP(Transimission Control Manner) or using UDP(User Datagram Protocol) in a speedy manner based on the Application layer protocols like HTTP/s. Depending on transport protocol selected the larger data set is divided into smaller data chunks/segments. This is the layer where source and destination port number headers are also assigned to the data segments.
Popular Transport Layer Protocols:
TCP (Transmission Control Protocol):
Ensures all data arrives correctly.
Handles lost or corrupted packets.
Perfect for important stuff like emails and web browsing.
UDP (User Datagram Protocol):
Based on fire and forget mechanism, offers fast, connectionless data transmission without guarantee.
Perfect for streaming and gaming where speed matters more than perfection
The "we'll send it and hope for the best" protocol.
Network Devices operating on Transport Layer:
Transport Layer Firewalls
Load Balancers (Transport layer)
Stateful Packet Inspection Firewalls
Protocol Analyzers
Real-Life Analogy:
The kitchen prepares food in portions that are easy to deliver and assures its quality. In case something goes wrong, for example, they made a mistake in the order, they will remake it, and that is how it works with the recovery from an error. More specifically, TCP is a waiter who assures the order is perfect. UDP on the other side is like a buffet where you serve yourself fast; no checks are performed.
Network Layer: The Global GPS
Network Layer is responsible for transmission of data over the network. It is responsible for finding the shortest path to transmit the data segments to reach it’s destination over the network, also adds source and destination IP address headers to the data chunks and after this the segments are referred as packets(for TCP) or datagrams(for UDP).
Network Engineer Joke: "Why did the UDP packet cross the road? Because it didn't care if it made it to the other side!"
Popular Network Layer Protocols:
IP→Internet Protocol (IPv4 or IPv6): Routes packets between networks
ICMP (Internet Control Message Protocol): Reports errors and provides network diagnostics
IGMP (Internet Group Management Protocol): Manages multicast group memberships
Network Devices operating on Network Layer:
Routers
Multilayer Switches
Network Layer Firewalls
Real-Life Analogy:
The delivery service (e.g., Swiggy/Zomato) decides the best route to deliver food. Logical addressing is the delivery address (IP address) that the customer provides. The routing process is the driver choosing the most efficient path to customer’s location.
Data-Link Layer: The Local Traffic Cop
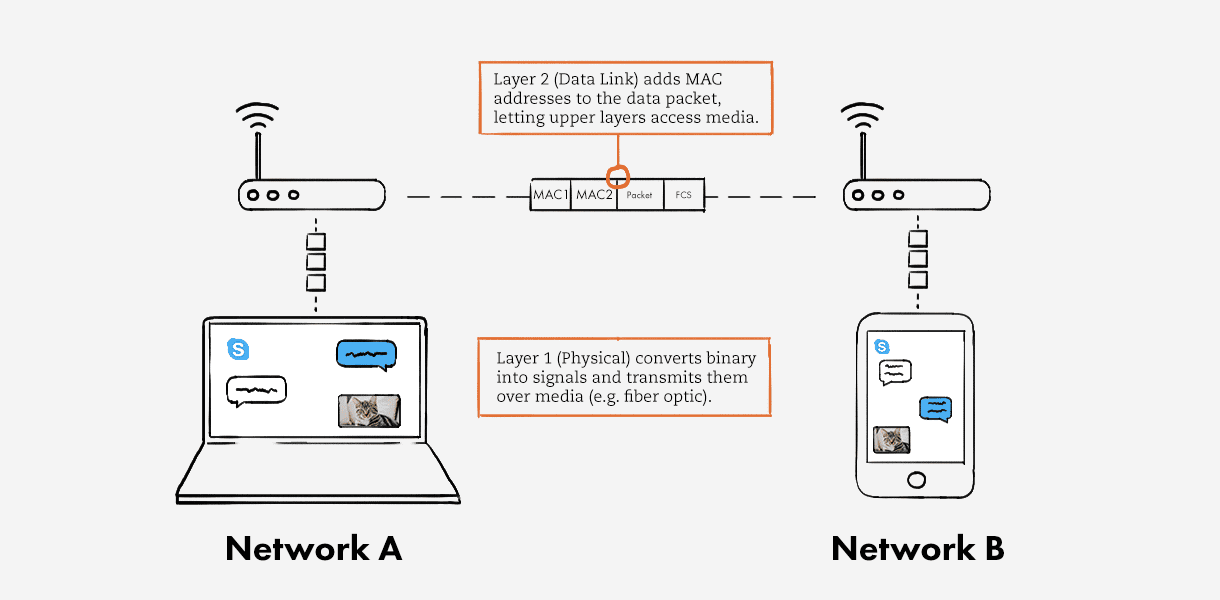
Data-Link layer is responsible for reliable delivery of frames between directly connected nodes and handles local addressing. This layer also adds source and destination MAC address headers to packets/datagrams and then these packets/datagrams are referred as Frames.
Popular Data-Link Layer Protocols:
Ethernet: Enables data transmission between devices on a local network
PPP (Point-to-Point Protocol): Establishes direct connections between two network nodes
HDLC (High-Level Data Link Control): Provides error control for transmissions
MAC (Media Access Control): Controls hardware addressing and channel access
Network Devices operating on Data-Link Layer:
Switches
Bridges
Network Interface Cards (NICs)
Wireless Access Points (WAPs)
Real-Life Analogy:
Within the restaurant, the food is placed on trays (frames) for delivery to the table. Each tray has a table number (MAC address) so the waiter knows where it goes. If the tray is dropped (error), the food is replaced.
Physical Layer: The Digital Highway
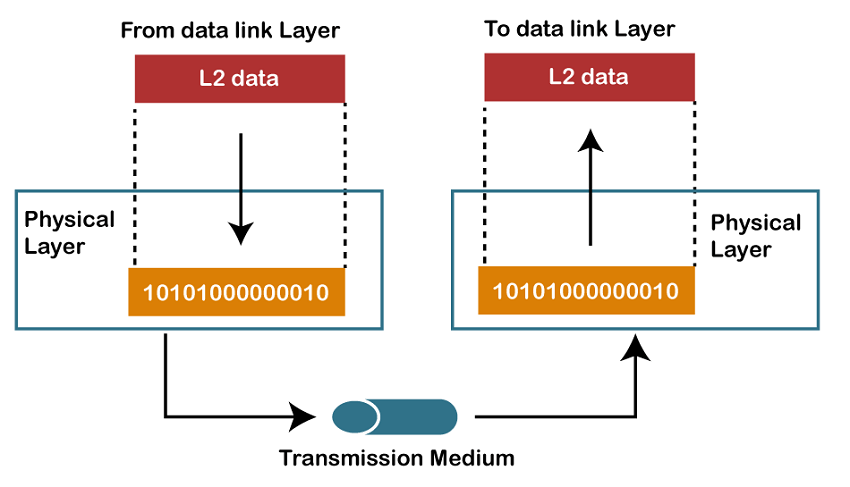
Physical Layer, the bottom layer of OSI model is responsible for converting data into physical signals(electrical signal, light pulses or radio waves) over the physical medium.
Popular Physical Layer Protocols:
DSL (Digital Subscriber Line): Transmits digital data over telephone lines
USB (Universal Serial Bus): Defines physical connection and power delivery standards
Bluetooth: Specifies wireless communication between devices over short distances
Network Devices operating on Application Layer:
Hubs
Repeaters
Network Cables
Fiber Modems
DSL Modems
Real-Life Analogy:
This is the infrastructure—tables, chairs, plates, and utensils in a restaurant. It’s the physical medium that makes the dining experience possible. Similarly, the physical layer consists of cables, switches, and wireless signals allowing network communication to take place.
Conclusion:
The OSI model is not just a concept; it's an indispensable resource for network communication. The OSI model simplifies the way we think about data flow and interoperability between diverse systems and technologies by breaking down complex processes into seven distinct layers.
Happy networking, and don't forget the classic network engineer's mnemonic: "Please Do Not Throw Sausage Pizza Away" (Physical, Data Link, Network, Transport, Session, Presentation, Application)!
Join the Discussion:
We appreciate your thoughts and experiences with OSI model! Kindly use the comment section to ask any questions, share your views, or discuss how you can apply this in real life.
Engage with Us:
👍 Did you find this article helpful? Give it a like!
💭 Share your favourite tech jokes in the comments.
🔔 Subscribe for more tech content that's educational and occasionally funny.
Share Your Feedback:
Your feedback helps us create better content. Drop a comment below about:
Your experience with OSI model.
Suggestions for future technical articles.
